How iTop VPN Encrypts Your Data and Shields Your Digital Life
In an age where electronic threats lurk behind every simple click, how protected are you currently when searching online? Have you ever wondered how a VPN like iTop shields your details from hackers, trackers, and your Internet Service Provider (ISP)? These usually are not just tech queries but inquiries about privacy, security, and regulation. These days, we dive into the heart of what powers iTop VPN: encryption know-how.
Let’s explain how iTop VPN will quietly but powerfully fortify your digital life in 2025.
What Is Encryption and Why Should You Care?
Imagine sending a letter, but before it leaves your hand, it is positioned inside an impenetrable vault with many locks. That’s what encryption does with your information. It transforms readable details (plaintext) into unreadable code (ciphertext), making it virtually ineffective to any individual without the vital.
But why does this matter?
In today’s hyper-connected planet, your knowledge of financial institution logins, private chats, and browsing practices is constantly at risk. Whether or not you’re in a café employing public Wi-Fi or just scrolling at home, your information can be intercepted. That’s where iTop VPN’s military-grade encryption measures come in.
Military-Grade Encryption: The Gold Standard
iTop VPN utilises AES-256 encryption, also known as Advanced Encryption Standard, having a 256-bit key size. This encryption standard is used to protect data in wireless communications, cloud storage, databases, mobile applications, and more. With its speed and strong security, AES has become the preferred method for protecting data in industries ranging from healthcare to finance.
Cracking AES-256 by brute force would take longer than the universe’s age. This suggests that every bit of information is wrapped in ultra-safe electronic armour. Whether you are accessing sensitive data files, using online banking, or just chatting with friends, your connection is safe from even the most determined cybercriminals.
Protocols That Power the Protection
Encryption isn’t just about scrambling information. It’s about how the information travels. That’s where VPN protocols come in. iTop VPN supports many stability protocols to present users with flexible and efficient alternatives based on their needs. Enhance your understanding by reading our in-depth post on Best PDF Viewer JavaScript Alternatives.
1. OpenVPN (UDP & TCP)
Open-source and battle-tested, Open VPN is reliable and secure.
● UDP is faster and perfect for streaming and gaming.
● TCP is more stable and ideal for web browsing and secure connections.
2. IKEv2/IPSec
This protocol is excellent for mobile users and quickly reconnects if the internet drops, which is a big win for anyone who hops between networks.
Quote:
“Encryption is not just for the paranoid; it’s for the proactive.” Cybersecurity Analyst, 2024
Kill Switch: The Last Line of Defence
Even the strongest fortress needs an escape plan. What happens if your VPN connection suddenly drops? Your data could leak instantly without you knowing.
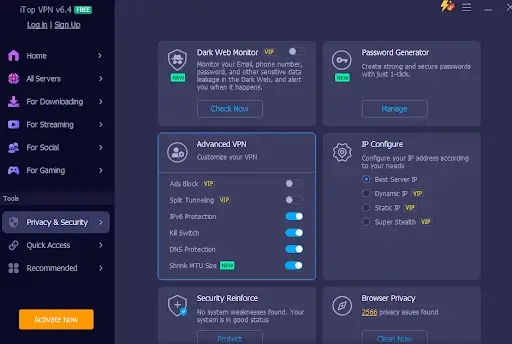
That’s why iTop VPN features a Kill Switch element. Should your safe link be interrupted, the Destroy Switch mechanically blocks all internet activity to prevent unencrypted data from staying exposed.
Think about it like a trapdoor that slams shut when someone attempts to peek inside.
DNS Protection & Anti-Tracking Tech
Encryption is simply a Component of the equation. DNS (Domain Name System) requests that typing “google.com” and going to that web page can leak your online conduct, even if encrypted.
iTop VPN features DNS protection that routes your queries through secure servers, so no one, not even your ISP, can see which Internet sites you might be visiting.
Anti-monitoring engineering also ensures that advertisers and third-party trackers can’t build a profile based on your browsing behaviour. Your digital fingerprint? Cleaned.
Cross-Platform Security, Seamless Experience
iTop VPN’s encryption doesn’t end on your computer. It travels with you. Whether or not you are on Windows, Mac, iOS, or Android, your connection stays regularly shielded across just about every device you employ. Whether or not you are dealing with sensitive do-the-job files from your laptop, scrolling through social websites on your tablet, or checking email messages on your smartphone, iTop VPN ensures that your data is locked and encrypted in an encrypted tunnel, irrespective of the platform. Find valuable tips and strategies in our article about iTop VPN.
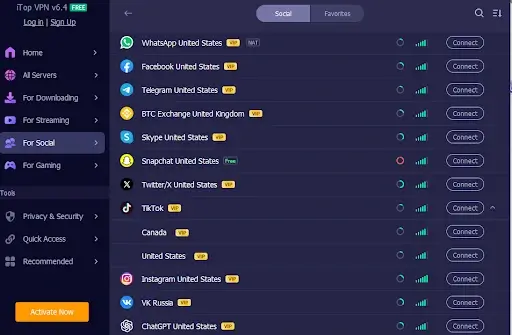
In this article, what can make it better yet is that you don’t have to be a cybersecurity specialist to take pleasure in best-tier protection. iTop VPN is built with serious people in mind. It’s a clean, user-welcoming interface that normally takes every effective encryption tech, functioning at the rear of the scenes and distils it into uncomplicated, intuitive controls. With just a few taps or clicks, you can secure your link, change servers, or activate Sophisticated options with no jargon, no problem, no worry.
The Human Impact: Why This Matters
Encryption can sound like an abstract concept. But this is real life:
● A journalist in a restrictive country using iTop VPN to safely access global news
● A student protecting personal data on a public university network
● A business owner securing sensitive client communications while travelling.
These are everyday people, not hackers or spies. They value their privacy, and iTop VPN gives them the tools to protect it.
Want Better Privacy in 2025? Here’s Your Move
Internet privacy is not a luxury. It’s a necessity in today’s hyper-connected world. iTop VPN has provided users with more than 3200 reliable and high-quality servers in 100+ locations distributed around the world. One-click to connect to any place you want. With cyber threats evolving and information breaches becoming far more advanced, controlling your electronic footprint is not just intelligent. It’s vital. That’s where iTop VPN measures in, going considerably beyond the basics of masking IP addresses.
This isn’t just a different VPN; iTop VPN is creating a Digital fortress around your internet activity. Leveraging armed forces-quality AES-256 encryption ensures your information remains untouchable, even on unsecured community Wi-Fi networks. However, the security doesn’t prevent them. With intelligent protocol switching, genuine-time kill switch defence, and DNS leak prevention, iTop VPN adapts to real-time threats, ensuring your connection is never exposed.
Final Thoughts:
It’s not about privacy. It’s about relief. Whether you’re streaming, searching, banking, or simply browsing, iTop VPN keeps your identity locked tight and your activities invisible.
So, are you prepared to stop becoming vulnerable on the web? With a top VPN, you’re not just accessing the World Wide Web; you’re also owning your privacy, one person-encrypted link at a time.
Download iTop VPN now and make your privacy a priority. You can visit Fintechzoom.com for more trending posts.



